Hacking HTTP Basic Authent...
Hacking HTTP Basic Authentication Dictionary Attacks With Burp Suite Free

Hacking http basic authentication dictionary attacks with burp suite free is our tutorial for today, we will use a tool called BURP suite.
If you just hear about BURP suite, here is the explanation from their website:
Burp Suite is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application's attack surface, through to finding and exploiting security vulnerabilities.
Burp gives you full control, letting you combine advanced manual techniques with state-of-the-art automation, to make your work faster, more effective, and more fun.
While writing this tutorial, I have no relations with portswigger.net, I write this tutorial on my behalf.
Explanation about HTTP basic authentication.
HTTP supports several authentication mechanisms. Upon a request for resource within a protected space the server should respond with authentication challenge using WWW-Authenticate header. In order to receive authorization the client should send requested identification information using Authorization header. When the client is not authorised a 401 “Unauthorised” response status is returned.
The simplest and most common HTTP authentication in use is Basic. The clients need to provide the credentials in a Base64 encoded string username:password. If the credentials are correct the web server returns the requested resource otherwise the server repeats the authentication challenge.

Requirements:
1. Download BURP suite at portswigger.net (in this tutorial I use the free edition) and install it.
2. Download the PHP login script I've already made to test BURP suite locally.
| Download |
Hacking HTTP Basic Authentication Dictionary Attacks with Burp Suite Free:
1. The PHP script on requirement number 2 is a simple log in page. You can copy it to your HTDOCS folder if you use XAMPP or WAMP for your web development platform. The picture below is the preview when I try to access it on my local system.

2. Run your BURP suite and change your browser proxy setting to run through BURP application. By default BURP will use port 8080, if you don't know how to change the browser proxy settings, you can view the tutorial how to configure browser proxy.
3. When proxy already set up, now we can access the login.php file. In this example, for testing purpose, I will input username = test and password = test. When we click the submit button(LOG IN), BURP will intercept the data as shown in the picture below.

Right click and choose "Send to Intruder".
4. On INTRUDER –> POSITIONS tab, change the attack type to "Cluster Bomb".

5. After finished setting up the attack type, we can move to PAYLOADS tab. To fill this PAYLOADS, see the picture on step 4
Payload set 1 = PHPSESSID (the value)
we will set up the same PHP SESSID value, because the system use a static PHPSESSID.

6. Now we will change the payload set number two, we're still on PAYLOADS TAB.
Payload set 2 = username (the value)

you can load the username data from username list. On the above example I input the username one by one.
7. On payload number three we will input the password.
Payload set 3 = password (the value)
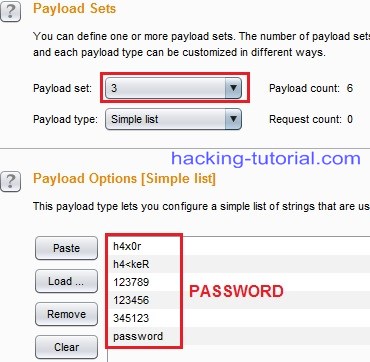
on this step you also can load from a password list, but in above example I input the passwrd one by one.
8. The last PAYLOADS to set up is the submit parameter.
Payload set 4 = submit (the value)
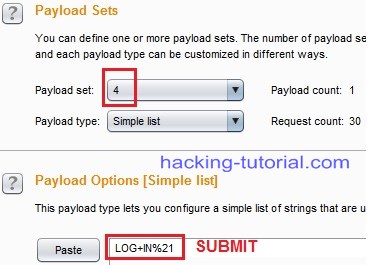
since this submit is to check whether user click the button or not, we can make it the same value LOG+IN%21.
9. Every PAYLOADS has been set up successfully, now we will start the attack and watch BURP suite perform the attack automatically. Click Intruder and choose "Start Attack".

10. BURP suite itruder will check the username and password one by one. When there's matching username and password, you can view the length was changed. From this example we know that the username = admin and password = 123456
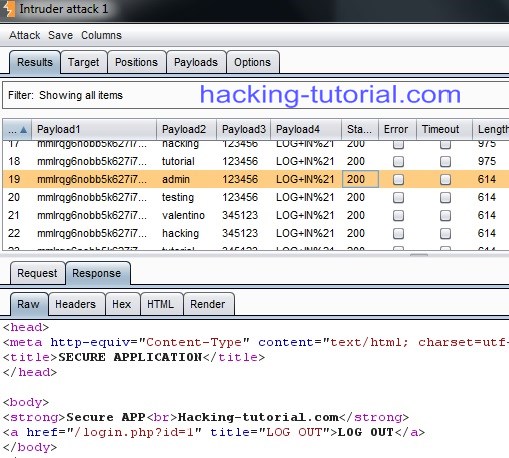
Conclusion:
1. To prevent this kind of attack, as a user you can do nothing, as developer you can do like GMail anti brute force system where every trying is logged by the system based on their IP address. If you try to log in and failed for several times, the system will force the user to solve the captcha.
2. As a developer you can do add the salt into username and password to make attack time much longer since you've add the salt, but in my opinion the first conclusion was better.










